
Fully Managed IT
Fully managed IT support for your business, with everything included.
All the services your business needs in one monthly package.
Simple pricing - everything included, per user, per month.
No extra costs, no add-ons.
Standard Plan - what’s included?
-

Managed IT
Fully managed IT support for your business, with everything included.
All the services your business needs in one monthly package.
Simple pricing - everything included, per user, per month.
-

Everything under one roof
Make everything our problem.
One phone number to call for anything IT.
We’ll take any IT issue off your hands and deal with it on your behalf.
-

IT Budgeting
We’ll work with with to plan your IT budgets and keep costs under control.
All of your subscriptions and hardware replacements are tracked with monthly reports so there aren’t any nasty surprises from an unexpected license renewal.
-

Close relationship with our clients
We work extremely closely with our clients, getting to know their business inside-out.
You’ll get a dedicated primary and secondary account manager that will work closely with you.
We hold regular meetings with you to help you get the best out of your IT.
-

Device management
Fully cloud-based device deployment & management.
Minimise downtime and improve staff productivity.
Centralised settings and policies are applied to all devices automatically from the cloud.
-

Seamless device deployment
Ship new devices directly to staff, wherever they are in the world and have all of their apps and files automatically deploy to their device.
-

App deployment & management
We’ll automatically manage and deploy third-party apps to your devices.
Fully automatically from the cloud.
Apps can even be deployed by role or department; Make sure the marketing team have Photoshop installed automatically and Finance have access to Xero.
-

Patch Management & Software Updates
Ensure your devices are always kept up to date without annoying your team.
Critical updates are applied silently out of working hours, keeping you protected and your staff working.
-

Guaranteed SLAs
We aim to deal with all critical issues within 5 minutes.
All of our agreements include SLAs, giving you piece of mind that important issues are dealt with immediately.
-

Centrally managed Email Signatures
Automatically apply your company signatures on every device, every time.
Images and formatting display correctly.
Job titles and phone numbers pulled automatically from Microsoft 365 for each person.
Include personalised photos for each staff member, straight from Microsoft 365.
-

Email & Microsoft 365 backup
All of your Email, Contacts, Calendars SharePoint and Teams data is backed up automatically at least once a day.
Deleted that tender document you’ve spent all week on? Not a problem.
-

Email deliverability & reputation monitoring (DMARC)
Not sure if clients are getting your emails?
DMARC ensures only authorised senders can send from your email address, leading to higher levels of trust with other email providers.
Block malicious impersonation of your brand and identity automatically.
-

Asset & warranty management
Asset & warranty reports are sent out monthly with a full list of your IT inventory, including any software licenses and subscriptions.
This allows you to easily budget your IT spend and identify any upcoming renewals or replacement expenditure so you don’t have any unpleasant surprises.
-

Documentation system & Standard Operating Procedures
We maintain a documentation system and SOP (Standard Operating Procedure) system with simple, easy to follow guides built on your specific processes.
We’ll build dedicated onboarding and offboarding processes, along with any processes specific to your business.
We’ll give you access to look up any of the passwords we have recorded for you, 24×7.
-

Backup monitoring & reports
Our backup monitoring system automatically tracks your backups, alerting you if a device hasn’t sent in a backup report for more than a day or if a backup has failed.
A simple dashboard gives you a colour-coded overview of all of your backups.
Log into our portal or check your monthly or weekly backup email report emails.
Test restores and backup recovery processes are also logged in the system, with a full audit trail.
-

Vendor management
We’ll take on all your IT headaches - we’ll deal with the printer manufacturer or your web hosting company on your behalf.
-
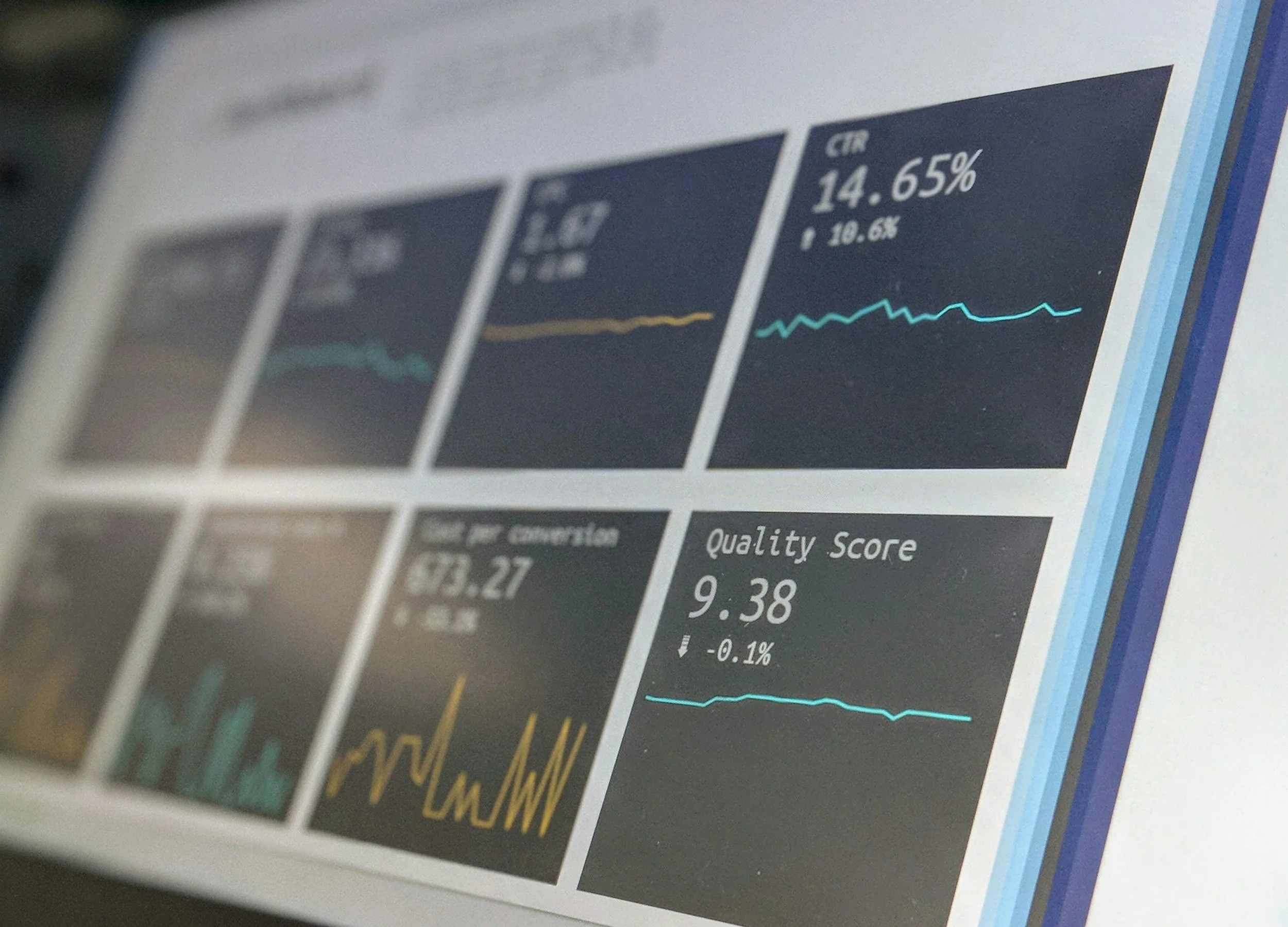
Monthly reports
Each month we’ll send out a full report on how we’re doing.
We hold ourselves to account - you can see how many issues you’ve raised, how long we took to fix them and any recurring issues.
-

Email & Microsoft 365 security
Secure your Email & Microsoft 365 - from encrypting your emails, junk and phishing filtering to automatic link and attachment scanning, we’ll keep it secure.
-

On-site support - INCLUDED
All of our agreements for over 5 users include on-site support as standard.
Our engineers are based across Oxfordshire, Hampshire, Gloucestershire, Northamptonshire, Leicestershire and Yorkshire, ensuring we’re always in easy reach for our clients.
Optionally you can opt to remove on-site support to reduce your monthly cost.
-

Hardware repairs
We’ll carry out repairs in our on-site workshop for your devices.
If your device has a warranty, we’ll deal with the manufacturer to arrange the repair.
-

Access your files from anywhere
Sync your desktop and documents across all of your devices automatically.
-

Your Brand front & centre
We’ll set up all of your services with your company branding, ensuring your IT systems put your brand front and centre to your clients.
-

Security
Full end-to-end security, from devices to cloud services.
Wrap-around security solutions which protect your business against the latest threats, regardless of the source.
-

Security best practices
All of our clients environments are kept aligned to security best practices, including the use of automatic security baselines.
Baselines automatically monitor our client’s environments and alert or automatically correct settings or policies in real-time.
-

Zero trust
“Never trust, always verify”.
Our systems utilise the Zero Trust model to ensure our clients data and systems are protected.
Your IT partner holds the keys to your kingdom in their hands. We take our responsibilities extremely seriously and are always reviewing the latest security practices to keep ourselves and our clients secure.
-

Cyber Essentials Certification
Get your business Cyber Essentials certified.
Whether you need it for a contract, tender or your piece of mind - we’ll get you certified.
Your devices are automatically monitored for compliance with automatic alerts if devices fall out of compliance (e.g. Disk Encryption disabled).
All work to bring you up to the required standard, all licensing and certifications costs are included.
-

Endpoint Detection & Response
Our advanced Endpoint Detection & Response solution constantly monitors all of your devices for suspicious activity and ransomware.
Infected or breached devices are automatically isolated, the threat remediated by our 24×7×365 Security Operations Centre and brought back online.
This secures your data and reduces downtime for your staff.
-

Identity Threat Detection & Response
Constant monitoring of all user accounts backed by our 24×7×365 Security Operations Centre.
Compromised accounts are automatically locked out and an investigation triggered to identify the cause and prevent further access.
Stop attackers before they can bombard your clients with phishing emails or gain access to client data.
-

Security monitoring & Threat lockout
Protect against threats with proactive security monitoring.
We monitor everything that flows across your networks, devices and apps, detecting and blocking novel threats backed by a 24×7×365 Network Operations Centre.
-

Security Awareness Training & Phishing simulations
Security awareness training helps employees become their own line of defense with episodes, phishing simulations and actionable reporting.
-

Secure password manager
Automatically store and fill your passwords.
Generate strong passwords and share accounts with your team, even with Multifactor authentication codes.
Breach monitoring alerts you automatically to any compromised accounts.
-
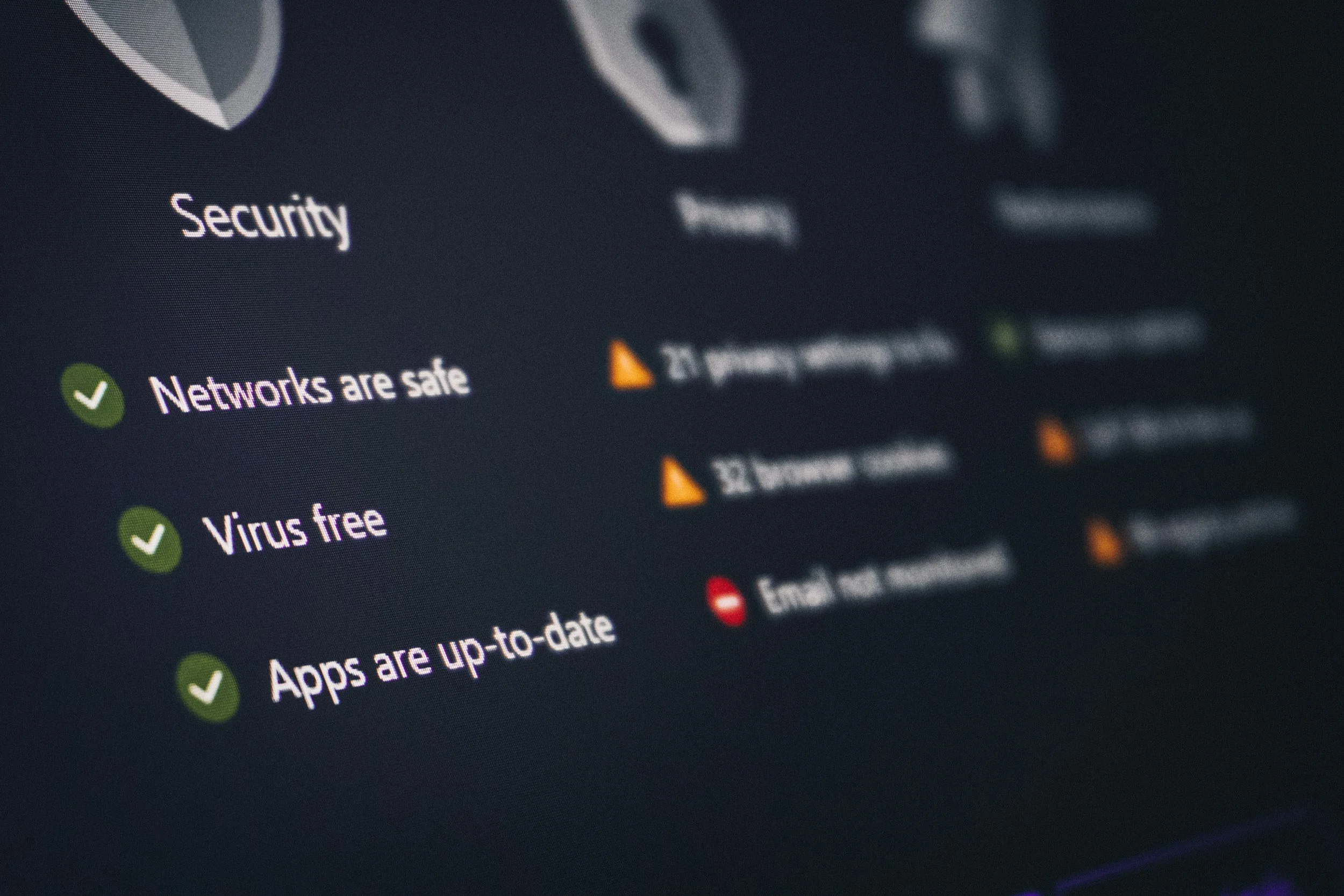
Web & DNS Filtering
Protect your staff against the latest threats, automatically blocking malicious websites and domain names.
Staff remain protected wherever they are, even on public Wi-Fi hotspots.
Ensure your staff stay productive by blocking time-wasting websites during working hours.
-

Vulnerability mangagement
Automatic monitoring of your apps and devices for the latest security vulnerabilities.
Critical vulnerabilities are patched before they can be exploited, keeping you and your client’s data safe.
-
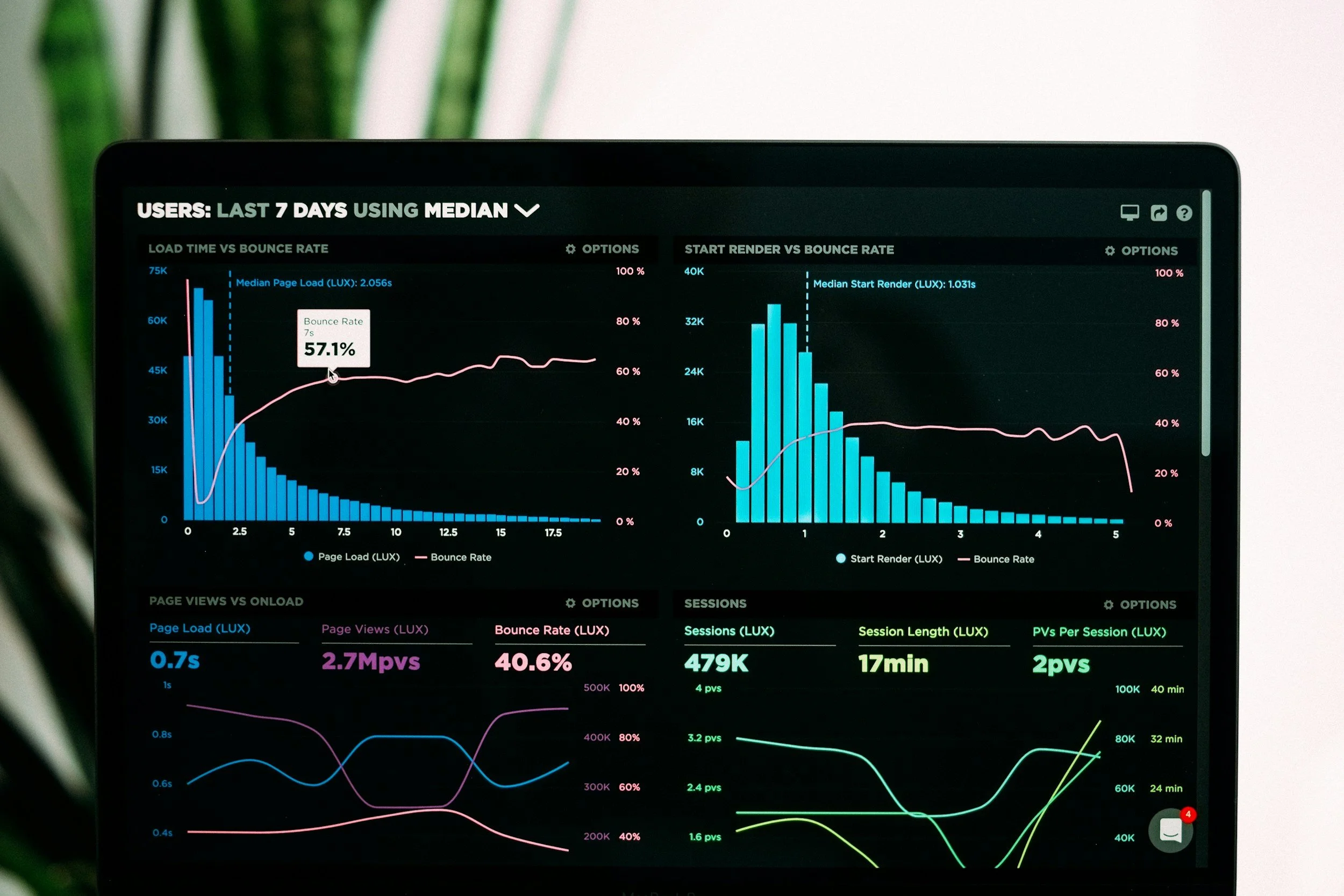
Remote monitoring
Remote monitoring of your devices & networks - automatic remediation to fix issues before you even notice them.
Low disk space? Printer not working? Not any more…
-

Device encryption
Automated device encryption across all your devices keeps your data safe, even if your laptop is lost or stolen.
-

Sales & IT Procurement
We’ll help you find the exactly the right product or solution for your needs.
Whether you need a new 4U rackmount server or a printer cartridge, we can help!
-

Microsoft 365
Management of your entire Microsoft 365 environment, including applying security baselines to keep everything aligned with industry security best practices.
-

Internet & Connectivity
We can supply and support a range of connectivity solutions for your business.
Already using another provider? - We’ll deal with your Internet Service Provider(s) and manage your internet connections for you, dealing that any issues that arise.
We’ll act as go-between, managing any issues on your behalf, getting issues resolved quickly.
-

DNS Management
We’ll manage DNS changes for your domain names on your behalf.
-

Adobe Creative Cloud
Full management of your Adobe Creative Cloud licensing and licenses.
-

Microsoft Azure
Management of your Microsoft Azure environment.
Enterprise Plan - what’s included?
-

Everything in the Standard Plan
All services, tools and apps in the Standard Plan are included, plus…
-

SIEM
Security and Information Event Management or SIEM, collects logs from all of your devices, apps and services and collates them all in one place.
These logs are constantly analysed for suspicious activity by our Security Operations Centre, providing early warning of potential attacks. Audit logs enable forensic investigation in event of a data breach, allowing you and your clients to see exactly what was accessed.
Required by many client contracts for large multi-national organisations.
-

Cyber Essentials PLUS certification
Demonstrates to your clients that you hold the gold standard of Cyber Essentials.
Includes a full audit by a certified auditor, checking to make sure all of your devices, apps and policies meet the required standard under Cyber Essentials.
Includes penetration testing of your networks and cloud services.
-

Email Signatures - PRO
Includes the Pro version of our Email Signatures tool.
Advanced scheduling / Social media feeds in signatures / Hubspot and salesforce integration / Centrally control backgrounds for video meetings
-

Password manager - PRO
Adds dark web monitoring / Advanced reporting / Alerts module for compromised accounts
